NIST 800-171 Security Summary
NIST security summary: If you are a government contractor, or you are trying to be a government contractor, chances are you have heard of NIST SP 800-171. And if you haven’t heard of NIST SP 800-171, you will certainly become familiar with it… At least you should, if you want to keep your government contract. And forget about even winning one in the first place if you are not NIST SP 800-171 compliant.
But let’s take a step back and get some perspective on what NIST SP 800-171 is and where it comes from!
If you have any questions, reach out to us on our forum!
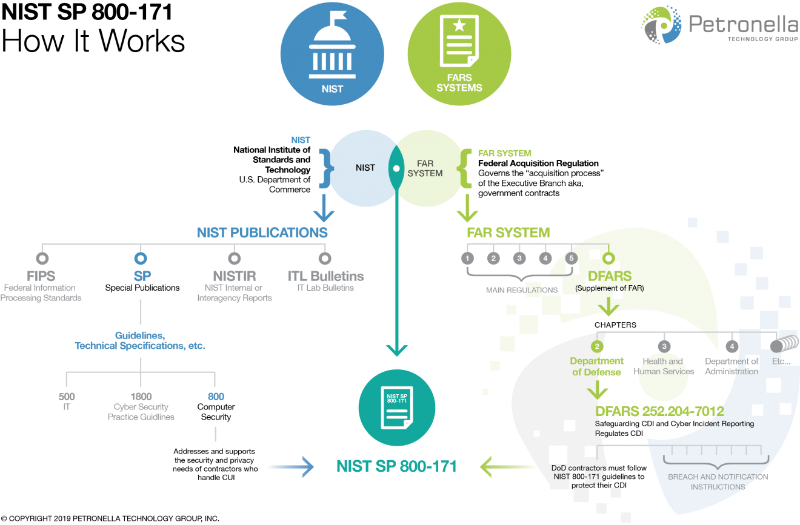
National Institute of Standards and Technology
The National Institute of Standards and Technology (NIST) has a deep-rooted history in the United States. Established in 1901 by the US Congress, the ongoing goal of NIST has been to promote the US economy by becoming an international leader in the development of measurements and standards. And they have largely succeeded (if you pointedly ignore the metric system, or lack thereof in the US).
Since its inception, it has maintained the same goal, but it has added to and expanded its objectives. In addition to promoting the US economy, NIST also issues and develops standards and guidelines that help protect sensitive information that is held within US federal agencies.

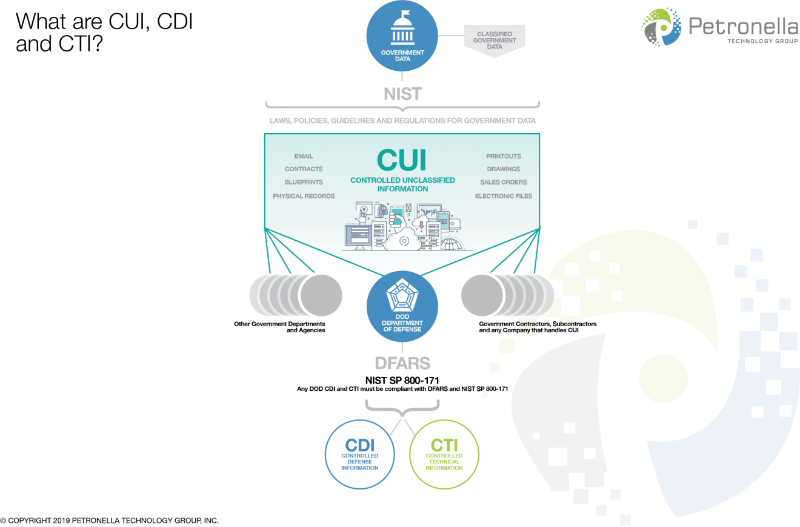
That’s great, but what does all this have to do with my business? Well, as you can imagine, government contractors play a large part in creating, transmitting and/or storing the sensitive “Controlled Unclassified Information” (CUI), which is simply any data and/or information used by US federal agencies. Which means that it has fallen on NIST’s shoulders to protect federal contractors and their supply chain. In fact, it has become a huge focus of NIST’s in the past few decades.
And for really good reason! Government contractors have been notoriously woefully lacking in data protection, it would be laughable if it wasn’t so potentially harmful to our national security… Especially in recent years, as hackers become more and more sophisticated while most contractors are lagging further and further behind.
It’s like being late to the train station because you were simply being lazy and not paying attention. You start running on the platform towards the train that is just leaving the station, and it’s going slow at first so you think MAYBE you can catch up, but the closer you get, the faster the train speeds away.
Or, in a lot of cases, it’s like you just stay on the couch eating potato chips and don’t even bother to get to the station, much less the platform.
OK, I get it. I’ve completely missed the cybersecurity train. Enough with the guilt, just help me understand more about NIST and how it relates to me. Fine, fine! So you understand why NIST was created and what its goals are, but how exactly does it reach its goals? It’s pretty simple, actually. They write and then they publish the writings.
NIST Publications
NIST standards are now recognized as THE standard for best practices in cybersecurity. There are four different types of publications put out by NIST:
- Federal Information Processing Standards (FIPS)
- Special Publications (SP)
- NIST Interagency Reports (NISTIR)
- Information Technology Lab Bulletins (ITLB)
For your intents and purposes, all you need to worry about are the SPs. That being said, NIST has published a plethora of SP series:
- 500 Series - For Information Technology
- 1800 Series - Which deals with cybersecurity
- 800 Series - These are guidelines for security compliance, and this is our main concern
- NIST SP 800-53: You may have heard of this SP if you have heard of 800-171. We will get into the differences between NIST SP 800-53 and NIST SP 800-171 in another article, but essentially this is a 460+ page publication with over 200 security controls. It outlines the precautions government agencies need to take to protect their data and their information systems.
- NIST SP 800-171: Aha! Finally, I get to the SP that is applicable to you and your business. NIST SP 800-171 outlines cybersecurity guidelines for contractors, such as yourself, who handle CUI. CUI is essentially data and/or information that you handle in any capacity, that is sensitive but not classified. NIST SP 800-171 is about half the size of the NIST SP 800-53. It has just over 100 pages and it has a total of 110 security controls, broken up into 14 different “families.”

NIST SP 800-171
Since you are now aware of what NIST is, and where NIST SP 800-171 came from, it’s time to get into the meat and potatoes of NIST SP 800-171. As mentioned above, it’s made up of 110 different security controls that are divided into 14 separate families. Those 14 families can be grouped into 4 main families:
- Controls
- Monitoring & Management
- End-User Practices
- Security Measures
We are telling you that because, instead of boring you with unoriginal content you can find with a simple NIST SP 800-171 Google search, we are going to talk to you about the four main groups.
NIST SP 800-171 Group 1: Controls
Control requirements regulate who can and can’t access CUI and how the data is handled by:
- Assessing and developing security controls
- Developing formal policies and procedures
- Creating and maintaining audit records
- Securely transmitting data
- Encrypting data at rest
NIST SP 800-171 Group 2: Monitoring & Management
The group of security controls deals with how you monitor the CUI that you handle and how you manage your data and processes through:
- Monitoring and managing user access
- Authenticating users and utilizing multi-factor authentication
- Establishing incident management process
- Patching critical systems and scanning for vulnerabilities
- Deploying antivirus/malware solutions
- Monitoring network traffic for malicious activity
NIST SP 800-171 Group 3: End-User Practices
Your employees are your biggest asset; but they can also be your biggest liability; afterall, phishing emails don’t click themselves. In order to mitigate the liability that is user error, you and your managers must:
- Provide training and awareness to end users and system administrators on proper procedures for handling CUI
- Define and execute minimum password complexity compliance
- Document how CUI is controlled by every department within the company
NIST SP 800-171 Group 4: Security Measures
When someone thinks of “cybersecurity,” this is probably what they tend to think of. To be compliant with NIST SP 800-171 security measures, you must:
- Assess and develop appropriate security controls
- Backup CUI securely
- Create and enforce policies preventing unauthorized software
- Identify, track and restrict access to ports
- Implement firewalls
As you can probably imagine, NIST SP 800-171 is rather complex. While it may seem like more of a nuisance than anything else, it has a purpose: to protect our national security. It is huge and scary and hard to implement, but there is hope! Contact Petronella Technology Group today to get more information about keeping your CUI (and your contracts) safe and secure! 919-422-2607 or [email protected]
.jpg)






